Samba
Tasks
Authenticating Samba against LDAP
The following steps will guide you on how to set up Samba to authenticate against a clean install LDAP server. I will be using OpenLDAP from the osixia/openldap docker image.
Once your LDAP server is ready, populate it with the required samba groups and users. The best way is to use the smbldap-tools package. On the samba server, install the following packages.
# yum -y install smbldap-tools samba samba-common-tools
Configure samba. At the very least, you should have the following in /etc/samba/smb.conf. You must specify a bind DN that has read/write access to the LDAP directory.
[global]
workgroup = WORKGROUP
passdb backend = ldapsam:ldap://ldap.home.steamr.com
ldap suffix = dc=home,dc=steamr,dc=com
ldap admin dn = cn=admin,dc=home,dc=steamr,dc=com
ldap user suffix = ou=users
ldap machine suffix = ou=computers
ldap group suffix = ou=group
ldap passwd sync = yes
ldap ssl = no
server string = Samba Server
security = user
hosts allow = 10.
log file = /var/log/samba/log.%m
Configure smbldap-tools. The configuration for this is at /etc/smbldap-tools/smbldap.conf. At the minimum, you should have this:
sambaDomain="WORKGROUP"
slaveLDAP="ldap.home.steamr.com"
slavePort="389"
masterLDAP="ldap.home.steamr.com"
masterPort="389"
ldapTLS="0"
suffix="dc=home,dc=steamr,dc=com"
usersdn="ou=users,${suffix}"
computersdn="ou=computers,${suffix}"
groupsdn="ou=group,${suffix}"
idmapdn="ou=Idmap,${suffix}"
Next, use the smbldap-populate tool to populate the LDAP directory. Note that a bunch of OUs, groups, and default users will be created. The tool will also ask for a new password for the root account that was just added to the directory.
# smbldap-populate
Populating LDAP directory for domain WORKGROUP (S-1-5-21-2049073866-1371207509-1214748462)
(using builtin directory structure)
entry dc=home,dc=steamr,dc=com already exist.
adding new entry: ou=users,dc=home,dc=steamr,dc=com
adding new entry: ou=group,dc=home,dc=steamr,dc=com
adding new entry: ou=computers,dc=home,dc=steamr,dc=com
adding new entry: ou=Idmap,dc=home,dc=steamr,dc=com
adding new entry: sambaDomainName=WORKGROUP,dc=home,dc=steamr,dc=com
adding new entry: uid=root,ou=users,dc=home,dc=steamr,dc=com
adding new entry: uid=nobody,ou=users,dc=home,dc=steamr,dc=com
adding new entry: cn=Domain Admins,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Domain Users,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Domain Guests,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Domain Computers,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Administrators,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Account Operators,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Print Operators,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Backup Operators,ou=group,dc=home,dc=steamr,dc=com
adding new entry: cn=Replicators,ou=group,dc=home,dc=steamr,dc=com
Please provide a password for the domain root:
Changing UNIX and samba passwords for root
New password:
Retype new password:
Next, add any users or groups as needed:
## Add a new group and user, then set their password
# smbldap-groupadd -a -g 1000 leo
# smbldap-useradd -a -u 1000 -G "Domain Users,leo" leo
# smbpasswd -a leo
Start samba. Check the local and domain SID. They should both be set to the SID of the newly created groups that smbldap populated. For example, if Domain Users has a SID of 'S-1-5-21-2049073866-1371207509-1214748462-513, then the local and domain SID on the samba server should be set to S-1-5-21-2049073866-1371207509-1214748462 (without the final -XXX value).
## Start samba
# systemctl start smbd
## Ensure domain SID is set. If it isn't, as shown below, you will need to find the domain SID and then set it.
# net getdomainsid
SID for local machine BNAS is: S-1-5-21-2431635136-3205909659-925170555
Could not fetch domain SID
## Find the domain's SID by looking at the SID value in the LDAP server.
# net setlocalsid S-1-5-21-2049073866-1371207509-1214748462
# net setdomainsid S-1-5-21-2049073866-1371207509-1214748462
If the local SID can't be changed, change it manually in the LDAP server.
At this point, the LDAP users you added via smbldap-useradd should be able to authenticate to this samba server.
Validating samba configuration
testparm to test the smb.conf file
Troubleshooting
NT_STATUS_INVALID_SID error from check_sam_security
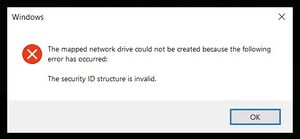
When trying to get the Samba server to use LDAP authentication, I was unable to get a user to properly authenticate. After entering a correct password, Windows will show a "The security ID structure is invalid" error.
On the samba server, the following messages are also visible in the logs:
[2021/07/20 11:39:01.893994, 0] ../../source3/auth/check_samsec.c:493(check_sam_security)
check_sam_security: make_server_info_sam() failed with 'NT_STATUS_INVALID_SID'
[2021/07/20 11:39:01.948641, 0] ../../source3/auth/check_samsec.c:493(check_sam_security)
check_sam_security: make_server_info_sam() failed with 'NT_STATUS_INVALID_SID'
[2021/07/20 11:39:01.989452, 0] ../../source3/auth/check_samsec.c:493(check_sam_security)
check_sam_security: make_server_info_sam() failed with 'NT_STATUS_INVALID_SID'
Additionally, pdbedit will show that some SID is does not belong in our domain and net getdomainsid will show that the domain SID is unavailable.
# pdbedit -L
sid S-1-5-21-356073995-1563379822-1369847962-1001 does not belong to our domain
# net getdomainsid
SID for local machine BNAS is: S-1-5-21-2431635136-3205909659-925170350
Could not fetch domain SID
The cause of this issue is that the samba server is not properly connected to the workgroup / domain. As a result, the NT_STATUS_INVALID_SID code will be returned during the authentication process.
Solution: When using just vanilla LDAP, the only way I am able to get the domain SID to match was to set it manually. This can be set by running:
## Set your domain SID
# net setdomainsid S-1-5-21-2049073866-1371207509-1214748462
You may also need to set the local SID to match. If this is required, you can use net setlocalsid or manually change it in the computer's object in the LDAP directory. In my experience so far, I had to manually change it in LDAP before auth works properly.
See Also
- Password sync: https://www.suse.com/support/kb/doc/?id=000016742