Web Proxy Auto-Discovery
The Web Proxy Auto-Discovery Protocol (WPAD) is used by organizations to automatically configure the proxy server on clients connected to a network. This is useful if the organization has network resources that are only accessible via a proxy server.
WPAD could be abused on an untrusted network (such as public WiFi networks) to configure your computer to use an attacker's proxy server and expose you to MITM attacks. While most operating systems support this protocol but have it disabled, Windows has this feature enabled by default which may be a security risk.
How it works
The location of the WPAD file is probed first from DHCP. With dnsmasq, the WPAD option is set with DHCP option 252.
If the DHCP server does not offer any information, attempts to obtain the file will be performed from a 'wpad' host on the network's domain. If the file does not exist, it will try again on the parent domain until it is at the root domain. For example, if the client is at pc.office.example.com, the WPAD file is obtained from http://wpad.office.example.com/wpad.dat, or if that fails, from http://wpad.example.com/wpad.dat. The file must be served with a MIME type of application/x-ns-proxy-autoconfig or application/x-javascript-config in order to be valid.
The wpad.dat file contains a proxy auto-config (PAC) script. This script defines a javascript function FindProxyForURL(url, host) which returns either DIRECT for a direct connection or the proxy protocol and servername PROXY proxy-server:port.
Security Issue
On a any network, an attacker could launch a MITM attack by setting up a rogue DHCP server and directing clients to the attacker's PAC file. All traffic would then be routed through the attacker's proxy server and users would be none the wiser since typically nothing warns the user a proxy server is being used.
Additionally, unlike a regular MITM attack where HTTPS is entirely protected, the use of a PAC script allows an attacker to expose the URL that you are accessing even with HTTPS. This could be done by leaking your URL by encoding it as part of the proxy server domain.
Disabling in Windows
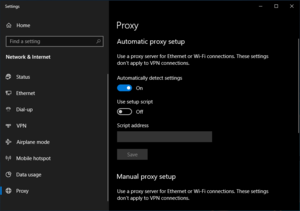
Windows 10
Open the settings window and search for 'Proxy Settings'. Switch the 'Automatically detect settings' to off.
Windows 7
Go to Control Panel, Network and Internet, Internet Options. Under Internet Properties, Connections tab, click 'LAN settings' button. Ensure that 'Automatically detect settings' is unchecked.